Article Summary
- FortiEDR and FortiNDR have different values in your cybersecurity portfolio. One is endpoint protection, and the other is network-level threat detection.
- It depends on your existing architecture, your budget, and whether your team needs finer-grained endpoint controls or more wide-ranging network visibility.
- Deploying them both as part of a SOC strategy provides customers with real-time, in-depth protection against advanced threats.
Modern threats require layered, proactive security; depending on a single detection point is no longer enough. As companies consider the right approach to harden their defenses, two stand out from Fortinet: FortiEDR and FortiNDR. They both play important roles in finding and eliminating threats like ransomware, advanced persistent threats, and zero-day attacks, but they exist at two different levels of your cybersecurity implementation.
Understanding their strengths, ideal use cases and integration potential is crucial for SOC teams and IT decision-makers who want to defend critical assets.
What Is FortiEDR and What Does It Protect?
FortiEDR (Endpoint Detection and Response) was created to deliver real-time, automated protection at the endpoint, where your network’s laptops, desktops, and servers constitute the points of entry. FortiEDR does not rely on signature-based detection (as regular anti-virus) but on behavior-based detection, machine learning, and automated response to prevent threats before they do any damage.
Key features include:
- Protection against Malware before it invades your machine.
- Post-infection cleanup: ID, isolate, and reverse any suspicious changes
- Real-time endpoint monitoring of zero-day attack signals
FortiEDR is ideal for organizations with remote or BYOD users, as it limits the attack surface where users connect to corporate resources.
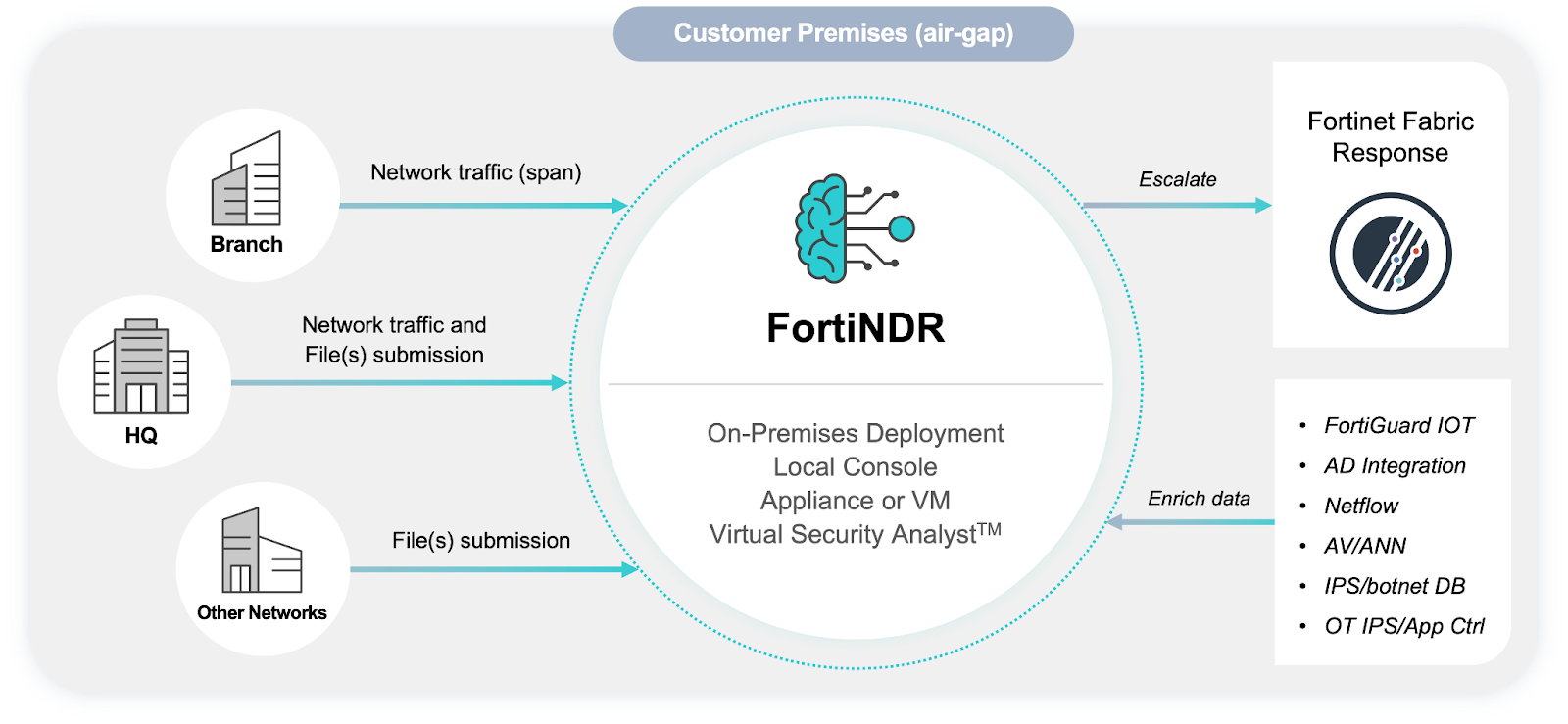
What Is FortiNDR and Where Does It Fit in the Network?
FortiNDR (Network Detection and Response) extends visibility to the network level, going beyond just the endpoint. It watches traffic among devices, data centers, and cloud environments to spot lateral movement, encrypted threats, and other anomalies that could slip past endpoint defenses.
With FortiNDR, you gain:
- Total network packet capture and analysis
- The detection of hidden threats within encrypted traffic using AI
- Support for SOC teams in threat hunting and forensics
FortiNDR is a great tool for threat hunting. It finds threats that come from within the network or move laterally once breached. It also assists in filling the visibility gaps encountered with endpoint protection alone in hybrid environments.
Key Differences Between Endpoint and Network Threat Detection
Understanding the distinctions between EDR and NDR is essential for building a balanced SOC solution:
| Feature | FortiEDR (Endpoint) | FortiNDR (Network) |
| Scope | Individual devices | Entire network infrastructure |
| Visibility | File-level, process-level | Traffic-level, flow-based |
| Response | Immediate, automated on endpoint | SOC-assisted, often manual |
| Deployment | Agent-based | Appliance or virtual sensor |
| Best for | Isolating threats at point-of-entry | Identifying internal spread or unknown origins |
These tools aren’t competitors; they are complementary. FortiEDR stops malware at the source, while FortiNDR watches for evasive or persistent activity that slips through.
When to Use FortiEDR, FortiNDR, or Both
- Employ FortiEDR when your organizational needs demand robust control at the endpoint level (particularly with a distributed or hybrid workforce).
- Deploy FortiNDR when you need centralized network visibility, manage multiple data centers, or wish to conduct more advanced threat hunting.
Deploy both when converging your endpoint and network telemetry for a real-time, orchestrated defense.
Many companies begin with one and grow into the other as their security maturity develops. However, using both simultaneously expedites the correlation of incidents and chops down dwell time.
Integration Benefits of Using Both Tools Together
FortiEDR and FortiNDR are integrated into the Fortinet fabric. Fortinet’s sustainable interconnected architecture facilitates integration between FortiEDR and FortiNDR. This unification enhances:
- Threat correlation: Endpoints and networks are linked to provide the whole picture.
- SOAR capabilities: Automation playbooks and policy-driven responses are provided by both tools
- Efficiency: Analysts get fewer false positives and more context for each alert
You can see how these capabilities combine to work in a real-world deployment on Liquid Networx’s FortiEDR and FortiNDR threat detection page.
Aligning Detection Tools With Your Security Architecture
Whether your business is constructing a Zero Trust architecture or bolstering an existing SOC, integration is fundamental.
FortiEDR: Seamless with Endpoint-Centric Approaches such as ZTNA FortiEDR is a perfect tie-in with endpoint-based approaches, such as ZTNA.
On the other hand, FortiNDR supplements that with centralized traffic inspection methods, similar to what is done with network access control (NAC).
For Liquid Networx Managed SOC customers, these tools are available and can be deployed on a managed basis with full life cycle support, from installation to 24/7 monitoring, to maximize ROI.
Budget and Resource Considerations and How LNX Can Help
Trade-offs between cost and capability are inevitable. FortiEDR and FortiNDR can be customized to the size of your organization, level of risk, and compliance requirements. Used tactically, they increase the ability to respond while decreasing the response time, eliminating duplicate alerts, and cutting costs in managed security operations.
Our team won’t leave you in the dark about managing these tools as part of Managed SOC services from Liquid Networx. We manage the tuning, integration, and escalation processes, allowing your internal organizations to concentrate on their business-critical activities. You can also learn more about endpoint protection via our solution page.
If you’re deciding which tools are reasonable in your environment, talk to our security architects about a strategy session. This session is designed to assist you in aligning detection technology with your business results and compliance status, reassuring you about your security decisions.
