What is EDR?
Remember the sinking feeling when you realize you’ve left your front door unlocked? Now imagine that same vulnerability applied to your entire digital world. Cyber threats are no longer reserved for corporate giants; businesses of all sizes are targets and face the same potential for data breaches, financial losses, and reputational damage.
This is where Endpoint Detection and Response (EDR) emerges to offer a game-changing level of protection for companies of all shapes and sizes. Unlike traditional security solutions that simply guard the perimeter, EDR looks deeper into the network, monitoring every endpoint – laptops, desktops, servers – for suspicious activity. It analyzes this data in real-time, using advanced techniques like machine learning, to identify suspicious behavior that might indicate a cyberattack.
Endpoint security has undergone a remarkable transformation in recent years, adapting to the ever-changing landscape of cyber threats.
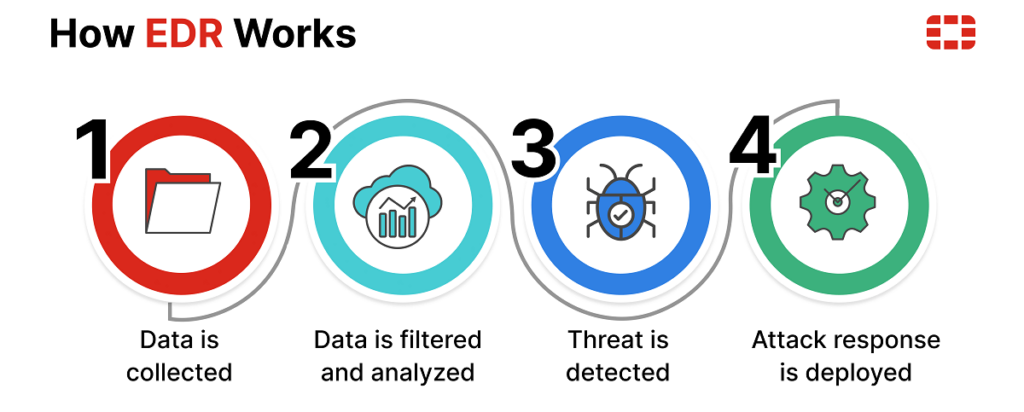
Why is EDR a game-changer for businesses of all sizes?
Level the playing field:
Regardless of your budget or infrastructure, EDR empowers you with advanced threat detection capabilities previously reserved for large enterprises. Thanks to services in cyber security offered by trusted cyber security service providers, this cyber security solution is now accessible to businesses of all sizes.
Take a proactive approach:
EDR proactively hunts threats before they strike, giving you precious time to respond and minimize damage. This proactive approach is essential in today’s ever-evolving threat landscape, keeping your team focused and productive.
Find the soft spots:
Gain unprecedented visibility into your entire network, uncovering hidden vulnerabilities and blind spots often exploited by attackers. This deeper visibility is crucial for making informed decisions and strengthening your overall security posture.
Swift action, minimal impact:
EDR enables rapid response, allowing you to isolate infected devices, block malicious activity, and minimize damage before it spirals out of control. This rapid response capability is key to minimizing downtime and protecting your critical data.
Be confident in your capabilities:
Protect your data, systems, and reputation with a robust security system that gives you and your employees the confidence to focus on growth. EDR provides peace of mind knowing you have a powerful cyber security solution in place.
EDR is not just a luxury; it’s a necessity in today’s digital landscape. Whether you’re a bustling startup or a well-established company, don’t wait until it’s too late to invest in your cybersecurity. Contact a trusted cyber security solution provider today and discover how EDR can transform your security posture and empower you to thrive in the ever-evolving threat landscape.
EDR features that are revolutionizing cybersecurity:
Defense: It doesn’t just wait for attacks to happen. EDR actively hunts for threats, identifying them even if they bypass traditional defenses.
Response: Forget waiting days to understand an attack. EDR provides instant insights, allowing you to respond quickly and minimize damage.
Visibility: It offers a comprehensive view of your entire network, exposing hidden vulnerabilities and giving you full control over your security network. This deeper visibility, facilitated by cutting-edge EDR services, is crucial for effective threat detection and prevention.
Action: EDR can automatically isolate infected devices, block malicious activities, and even roll back harmful actions. This swift action, a hallmark of reliable EDR services, minimizes downtime and protects your critical data.
Ready to level up your EDR?
EDR is not just a security solution; it’s a strategic investment in your business’s future. By adopting EDR, you gain a proactive defense against ever-evolving cyber threats, ensuring your data, systems, and reputation remain protected.
Get in touch with Liquid Networx today to learn more about how EDR can transform your security posture.
Get a Quote
"*" indicates required fields
